Business Operations
IT Best Practices: Do You Need Cybersecurity Insurance?
As we’ve discussed in the past, there are countless cyber security tools and best practices to help mitigate the effects of a data breach as well as the impact they may have on SMBs. As the technology landscape…
ContinuedHow to be Productive in Life: Avoid Distractions and be Productive in a Tech-Filled World
Trying to accomplish tasks each day can prove nearly impossible with the constant pings, notifications, and alerts coming from your devices. All seemingly urgent, expertly crafted messages designed to pull you away from what you are doing. Here are some great tips and tricks to maintaining focus during those busy days…
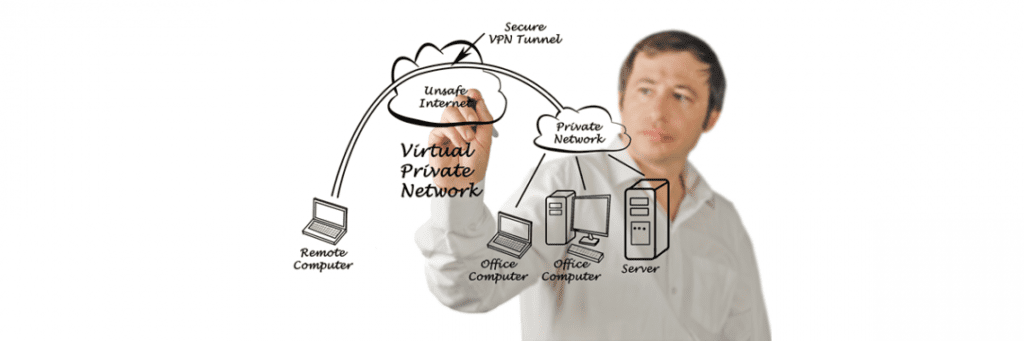
ContinuedWhy The Opera Free VPN Should Matter To You
Opera’s latest update has introduced a free integrated Virtual Private Network (VPN) for all users. With the barrage of stories pertaining to leaks and personal information becoming public, the announcement of a mainstream browser offering unlimited VPN access through their browser was incredibly exciting! So let’s delve into what it all means…
ContinuedIT Security Best Practices for Offboarding: Mitigating Risk During an Employee Dismissal
Terminating employees is one of the most unpleasant aspects of managing people, learn how to properly plan and prepare for a dismissal from an IT standpoint…
ContinuedPassword Management Best Practices: The Importance of Strong Passwords
We all know strong passwords are the backbone to maintaining a secure network. With more of our private communications, banking, and health information being stored online, the security risk to our most personal data becomes an even greater danger. Creating a strong password is the first line of protection to your information; but how are we intended to remember the vast number phrases and special characters to gain access? More…
ContinuedIT Support Services: Modern Proactive Maintenance
Maintenance Services for Computer were a very big part of Technical Services in the 1970’s and 1980’s. In those days, computers used to be much bigger than current PC’s and contained a lot of electronics and removable parts. In most cases, even mini-computers required to be installed in a dedicated and controlled environment (Server Room). Most of the maintenance tasks were physical and included shutting down the computer, cleaning up…
ContinuedCategories
- Backup & Disaster Recovery
- Business Operations
- Case Studies
- Cloud Services
- Cyber Security
- Employee Spotlight
- Finance & Budgeting
- Glossary Term
- Governance & IT Compliance
- Managed Services
- Mobile Device Management
- Network Infrastructure
- NIST 800-171 & CMMC 2.0
- PCI
- Podcast
- Project Management
- TSI
- Uncategorized
- vCIO
Cyber Security Policy Starter Kit:
10 Critical Policies That Every Company Should Have in Place