Blog

How to Maintain NIST 800-171 & DFARS Compliance as a Contractor With CUI
With the recent news that DFARS compliance requirements will start being enforced, we’ve seen a significant increase of questions concerning the role and application of ‘Government’ licensing- such as Office 365 Government or AWS GovCloud- for contractors possessing Controlled Unclassified Information (CUI). Aside from adhering to DFARS compliance itself, Government licensing- notably for Office 365 Government- is extremely expensive from both a subscription and implementation standpoint, and in turn, an area of concern for many contractor organizations. However, we’ve recently learned from Vicki Michetti- Director of the DoD’s Defense Industrial Base (DIB) Cybersecurity (CS) program- that CUI contractors don’t necessarily need these types of government licenses to comply with DFARS security controls because products like Office 365 Government and AWS GovCloud that have ATOs at the FedRAMP Moderate level. However, although CUI contractors can use these solutions, there are still factors to consider when evaluating these government level subscriptions and how they’ll potentially impact your compliance posture.
The DFARS/FedRAMP Security Requirements
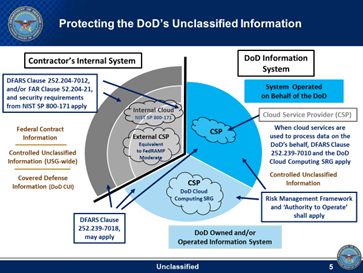
Clause 252.204-7012 provides a degree of clarification regarding these security measures- including the required capabilities of the solution controls themselves- needed by contractors to adequately protect the DoD’s CUI. The requirements outlined throughout paragraphs c through g of 252.204-7012 clarify that government edition subscription licensing- for any and all cloud service providers (CSPs)- isn’t necessarily required if the non-government level software license is FedRAMP Moderate- such as the case with Office 365 Government and AWS GovCloud- and meets the outlined DFARS control and compliance requirements. So as long as your CSP’s solution can provide the degree of incident reporting and forensic analysis required to meet these standards, it will be considered as an acceptable solution with the authorization to operate.
As outlined within Section (c) (Cyber Risk Reporting Requirement), contractors must report- per the instructions from the DoD cyber incident reporting webpage http://dibnet.dod.mil – security incidents that affect an information system subject to DFARS and/or those that impact a contractors’ ability to meet the requirements specified within their contract. They must review the evidence that CUI was compromised, as well as disclose the compromised systems and the data and user accounts as well. This review must also include an analysis of any other information systems that may contain compromised information associated with the incident.
Under Section (d) (Malicious Software), contractors must also submit any malicious software they discover and isolate during their investigation to the DoD Cyber Crime Center (DC3) in accordance with the instructions provided by DC3 or the Contracting Officer. Contractors must also preserve images of the information systems known to be infected in addition to all relevant data related to the monitoring and capture of malicious software. The contractor or subcontractor must also possess or acquire a DoD-approved medium assurance certificate to complete the report. For a more complete description of the process and attaining these certificates, simply refer to DoD’ Cyber Exchange resource site for more specific insights;
In addition to this, Section (e) (Media Preservation and Protection) contractors must also store the information pertaining to their cyber incident for at least 90 days after submitting the incident report to provide the DoD an opportunity to request the media. If the DoD does express interest in investigating a security incident further – Section (f) (Access to Additional Information or Equipment Necessary for Forensic Analysis)- the contractor must provide the DoD with the additional information or equipment needed to conduct a forensic analysis of the incident. If the investigation requires additional data or documentation, the contracting officer can also request the contractor to provide all the information on damage assessment that the contractor gathered during its investigation, according to Section (g) (Cyber Incident Damage Assessment Activities).
For a more complete description of the requirements outlined within sections c through g, refer to Clause 252.204-7012 for the compliance requirements themselves as well as the chart below;
https://www.acq.osd.mil/dpap/dars/dfars/html/current/252204.htm#252.204-7012
How Does This Impact your own Subs, Vendors, Partners and Non-Citizen Employees?
Essentially, contractors and all their sub-contractors, must have the DFARS compliance controls- and the considerations outlined within 252.204-7012- in place if they’re managing CUI in any capacity. However, there are exceptions for Commercial-off-the-shelf (COTS) distributors where DFARS compliance may not necessarily be required, as long as their CUI isn’t incorporated into the final product deliverable. However, it’s important to note, that many of these organizations- despite not needing to adhere to these requirements- are doing so, due to their prime’s own compliance requirements and/or preference. Simply put, any contractors who are functioning as distributors by incorporating CUI into modified COTS technology must comply with DFARS requirements. Contractors who merely use unmodified COTS products don’t need to be compliant, although DFARS compliance may be advantageous from a marketing or best practices standpoint- especially if their vendors or primes require or prefer that they do so. At the end of the day, DFARS compliance holds contractors accountable to adequately verify the compliance posture of their subcontractors- commonly known as “flow-down”- to ensure they comply with DFARS and Clause 252.204-7012 clauses. This requirement creates a trickle-down effect starting from the DoD, down to the subs of their prime contractors. Moving forward, if an organization’s subcontractors are out of compliance, they will be held accountable and can be penalized by losing their contract or in more serious cases, subject to legal ramifications such as fraud.
Another frequent question we receive pertains to a contractor’s non-citizen employees with access to CUI. It’s important to keep in mind that although non-citizens employed by contractors working with CUI do not conflict with your DFARS compliance posture, the prime contractors are free to make this a requirement within their contracts if they require specific citizenship or residency requirements, which could be outlined within section H of the contract itself.
In the event that an organization must adhere to International Traffic in Arms Regulations (ITAR) or Export Administration Regulations (EAR) standards that control the export of defense and military related technologies, then this data can only be shared with US persons- as defined within the regulation-, citizens and in many cases includes US corporations to determine a contractor’s ‘citizenship’ and eligibility requirements.
So, When Do You Actually Need Government Software Subscription Licensing?
Clause 252.204-7012 (b)(ii)(D) explains in further detail why Government level licensing isn’t always required for contractors managing CUI but how it may be a requirement in instances when manage classified information and CUI that is owned and operated by federal agencies.
“(D) If the Contractor intends to use an external cloud service provider to store, process, or transmit any covered defense information in performance of this contract, the Contractor shall require and ensure that the cloud service provider meets security requirements equivalent to those established by the Government for the Federal Risk and Authorization Management Program (FedRAMP) Moderate baseline and that the cloud service provider complies with requirements in paragraphs (c) through (g) of this clause for cyber incident reporting, malicious software, media preservation and protection, access to additional information and equipment necessary for forensic analysis, and cyber incident damage assessment.”
Unfortunately, we’ve encountered a number of cases where IT leadership and/or vendors mistakenly recommend these products to contractors managing CUI. Be aware that the most obvious reason to maintain this position- aside from simply misinterpreting these requirements- is that IT vendors stand to make a lot of money from Office 365 Government subscription sales and its very costly implementation due to not having a migration path. What does it mean to not have a migration path? Unlike a traditional migration to Office 365 where network settings, configurations and processes are simply transferred to the Office 365 cloud, migrating to Office365 Government will require you to rebuild your infrastructure from scratch which will amount to additional costs not including the implementation of the IT solutions addressing the DFARS controls.
Looking to the Future; The Importance of Strategic Partnerships
As these IT compliance requirements continue to evolve and with actual enforcement arriving in the near future, the role of IT professionals has expanded beyond the server room. In order to stay ahead of the curve, developing strategic partnerships with the government officials spearheading these DFARS initiatives will have to become an ongoing practice to ensure the successful strategic alignment between your IT compliance strategy and business objectives. Because both compliance requirements and business technologies are always changing, we encourage contractors to partner with service organizations that not only have in-house, IT compliance expertise but have a proactive, forward thinking, service model to accommodate today’s fast changing IT compliance and regulatory landscapes. States like California, Maine and New York have recently led the way toward implementing both commercial and consumer IT protection requirements, and MA based small businesses will only find it increasingly challenging to comply with new regulations once they inevitably become a reality. Today’s SME requires an IT partner that can forecast evolving IT compliance trends and their associated requirements, to ensure their successful continuity into the future and maintain industry competitiveness.
Keeping in mind these increasingly complex compliance requirements, we highly encourage that you routinely assess these factors and actively collaborate with your IT and compliance partners to verify your posture as well as accurately measure your risks.
“If you fail to plan, you are planning to fail.” – Benjamin Franklin
Final Thoughts
In short, Government level licensing isn’t required for CUI contractors unless specified in the contract or if the data the contractor has is classified or when a federal agency needs to store their own CUI or classified information with the CSP. This, alongside our other shared insights, are meant to help navigate these perceptibly convoluted requirements to help you more effectively address the IT security and compliance gaps within your strategy. If the stringent IT compliance requirements in states like California, Maine and New York are of any indication as to what may be coming to Massachusetts, this degree of collaboration will be needed to succeed within any industry and not just those that are DFARS required. Your security and compliance posture will become even more relevant as to how you’re able to conduct day to day business and will affect how your vendors will engage you- or your competitors- in their vendor selection processes.
Chris Souza is the CEO of Technical Support International (TSI), a New England-based IT support and cybersecurity compliance firm. He can be reached at: https://tsisupport.com.
It’s Your Move!
At TSI we understand how important DFARS compliance is. If you're looking for a partner who has a proactive, forward thinking service model to accommodate today’s fast changing IT compliance and regulatory landscapes, contact one of my colleagues at Technical Support International to schedule your introductory phone call.

Categories
- Backup & Disaster Recovery
- Business Operations
- Case Studies
- Cloud Services
- Cyber Security
- Employee Spotlight
- Finance & Budgeting
- Glossary Term
- Governance & IT Compliance
- Managed Services
- Mobile Device Management
- Network Infrastructure
- NIST 800-171 & CMMC 2.0
- PCI
- Podcast
- Project Management
- TSI
- Uncategorized
- vCIO
Cyber Security Policy Starter Kit:
10 Critical Policies That Every Company Should Have in Place


