Blog
What To Do After a Ransomware Attack
The topic of Ransomware is a steadily increasing mainstream topic affecting both small and large businesses alike. We’ve discussed some of these common types of intrusions before, this type of malware encrypts your data and holds it for ransom to receive the key, it requires a fast acting user in order to minimize the amount of damage it can cause to your machine or business infrastructure.
The aftermath of a ransomware attack can be catastrophic to any organization, often resulting in the loss of sensitive or proprietary information, not to mention the financial losses incurred from the restoration of files and harm to reputation. However, there are certain tips and tricks you can use to hopefully minimize the reach of an attack if you suspect one has occurred.
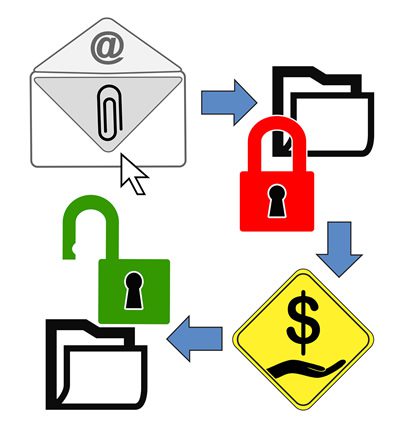
How it Works: Ransomware attacks generally start with an e-mail addressed to a recipient from a seemingly trusted source, with an attachment or URL provided. Upon opening what appears to be a legitimate attachment, such as an invoice or electronic fax, or clicking on the URL link, the ransomware code gets deployed onto your local machine.
After the code is deployed, the infection begins to encrypt files and folders on your local drives, any attached drives, backups, and potentially throughout the business network your machine is attached to.
Most users only become aware of the infection when they notice files are renamed, are unable to open a file, and/or receive a message with instructions to pay a ransom to unlock the data, often through an untraceable currency like Bitcoin. Even when an organization agrees to pay the ransom, there is no guarantee the perpetrator will actually offer the key to unencrypt your files or desist from extorting your network again.

Tips for Minimizing the Effects: in the event of a suspected attack, we recommend:
- Immediately disconnecting from the local area network (LAN) and/or any other storage devices connected to your machine.
- If you have a clean system restore point, you may attempt to go back to that data to see if it will work.
- If you have a recent backup you can format and reinstall Windows, then use your backed up data to make a fresh start.
- Try to identify the type of Ransomware that has infected your machine. With nearly 200 different forms of attack to date, identifying the ailment can help to identify a resolution. You can try a free service like ID-Ransomware to assist you in these efforts.
- If you are successful in identifying the type of ransomware that has infected your machine, check to see if there is an available decrypt tool.
- Finally, it is recommended you report the ransomware attack to the local cybercrime division of your police department, FBI office. You may also follow the FBI’s recommendation to file a complaint through their Internet Crime Complaint Center.
From the Experts: Unfortunately, ransomware continues to evolve and become more sophisticated the more it is proven to be profitable. There is no single tool of proven process to eliminate this very real threat to your organization. The best approach involves proper planning, including implementing a proper Backup & Disaster Recovery strategy, and educating users on the best practices for identifying a suspicious message. Of course, this is all in addition to having multi-layered protection for your organization; including enterprise level Anti-Virus, Anti-Malware, and Firewall which are properly configured. These are all a key component of having a trusted IT service provider who can minimize these vulnerabilities. To learn how we can help protect your organization, Contact Us today!
Confident with Your IT Strategy?
If you found the information in this blog post helpful and you'd like to discuss your business' technology strategy, then we'd be happy to hear from you.
Categories
- Backup & Disaster Recovery
- Business Operations
- Case Studies
- Cloud Services
- Cyber Security
- Employee Spotlight
- Finance & Budgeting
- Glossary Term
- Governance & IT Compliance
- Managed Services
- Mobile Device Management
- Network Infrastructure
- NIST 800-171 & CMMC 2.0
- PCI
- Podcast
- Project Management
- TSI
- Uncategorized
- vCIO
Cyber Security Policy Starter Kit:
10 Critical Policies That Every Company Should Have in Place


