Blog

The Reasons You Need a vCISO for CMMC Compliance
Today’s Business Need for a vCISO
There’s little doubt that the influx of new government regulations around privacy and data security requirements have become the primary area of focus for many DIB (Defense Industrial Base) and GSA contractors. These companies are now required to become compliant with a relatively new DoD mandate known as the Cybersecurity Maturity Model Certification (CMMC) which requires these contractors meet and sustain an on-going cybersecurity standard that range within five, increasingly more complicated Maturity Levels (1-5). It’s clear that companies of all types are struggling to meet these stringent mandates that will not only require the implementation of numerous, oftentimes complex, IT security solutions but also require internal resources to manage the process of maintaining their ongoing compliance programs. The need to develop and manage a security program in order to meet these compliance requirements exponentially increases the need for compliance expertise from an organization’s cybersecurity partners or existing IT teams and unfortunately, the responsibility to maintain the confidentiality, integrity, and accessibility of sensitive data gravitates to IT security leaders or to lead engineers who are already saturated with Tier1-3 type responsibilities. It soon becomes painfully clear, that many of these professionals do not have the knowledge, skills or experience to effectively address these demanding compliance requirements, resulting in a less than favorable CMMC audit outcome.
Your (v)CISO Options; Hiring Internally or Outsourcing
For larger organizations faced with these mandates, they typically hire a Chief Information Security Officer (CISO) who can manage information security issues and be responsible for securing their digital information or CUI. CISOs are seasoned IT Security professionals who have the breadth and depth of experience to help organizations establish a strong cybersecurity program, develop and adopt effective cybersecurity policies, and provide ongoing training to their IT teams. This includes reviewing existing programs and policies then adapting them to the ever- changing needs of the organization. They ensure the security posture of the organization is sufficient to the risks the organization must address and helps build resilience to better protect their environments from breaches that can cost them their reputation, fines, and contract revenue.
Unfortunately, this methodology leaves smaller organizations with two unrealistic options. The first is to overburden already straddled IT leaders with a responsibility that they do not understand, are not prepared for, and requires a significant amount of experience and effort to accomplish satisfactorily. The other is to postpone addressing the issue with the hope that it will go away. However, neither choice addresses the risk that can potentially be more costly than hiring a CISO in the first place.
Fortunately for small organizations, a third option has emerged that is both viable and cost effective; the Virtual CISO (vCISO). The vCISO can fill the role of CISO for any organization, without the cost and stress associated with recruiting, hiring and paying to retain a CISO. According to Forbes, there will be nearly 3.5 million unfilled security positions by 2021. If that continues to be the case, finding the talent and expertise to address your compliance requirements will only become more difficult and present real challenges when the need to address your security requirements becomes a need-to-have in order to compete for DoD contract opportunities.
Cost-Effectiveness
Without a doubt, one of the biggest benefits of outsourcing your CISO requirements is cost savings. Today, Chief Information Security Officers negotiate six-figure salaries, and a host of other benefits, due largely to high demand for their services in an increasingly regulated climate. For example, as of September 1, 2020, Salary.Com posted a CISO pay range between $196,232 – $334, 8301, with a median salary of $285,565, for the Boston, MA area. (CISO Salary, Boston 2020)
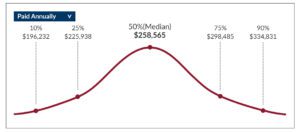
This obviously presents an issue to smaller organizations that may not have this budget or even need a full-time CISO. Hence, by choosing a vCISO, they only pay for what responsibilities and tasks that are needed to get the job done, and nothing more, no overhead as vCISOs typically work on a block-hour or per-hour basis, adding considerable value with significant cost reduction.
Expertise, Core Competencies & Objectivity
As no two organizations’ needs are alike, vCISO duties also vary depending on the company, compliance requirements and contract agreement terms. Their professional services offer scalability and flexibility to meet the evolving needs of any organization and provide immediate value due to their breadth of experience across the technical, security and compliance components of that role. A seasoned vCISO will also have established networks which can equate to corporate knowledge and add depth and resources beyond the organization’s means. vCISOs typically have ten or more years of experience and expertise in cybersecurity, have worked within various industries as security leaders and have attained industry-recognized certifications. This expertise is what a vCISO brings to the table alongside their established relationships with other security experts, vendors, and industry leaders that will help them perform at their best. With this type of hands-on experience and expertise, they can make security decisions that will drastically help your company’s progress and pro-actively address the gaps within your compliance posture.
As we’ve all seen before, oftentimes office politics can impact your compliance strategy’s success and it’s of the utmost importance to include an objective perspective that can help mitigate the impact of that type of environment. Power players, budget battles and precedent often influence security and compliance decisions to the detriment of a positive audit outcome. As an independent contractor, vCISOs provide objective advice void of company biases and are not subject to the various fiefdoms within a company. A vCISO arrives laser focused on a project, with a complete picture of what needs to be accomplished, how to accomplish it and a clear understanding of what auditors will expect, which all help lead to fact-based decisions supporting your security and compliance objectives.
Mature and Professionalize Your Security Program to Reduce Risk
As these compliance requirements become more stringent and complex, the ongoing process of managing and maintaining your security program becomes commensurately more complicated and unforgiving. Ensuring the successful execution of your compliance strategy and maturity level will require adequate planning alongside vCISO level capabilities and expertise to guarantee a successful compliance audit outcome. Although the implementation of the CMMC’s required technical solutions is a great start, a successful compliance strategy also consists of three major components that need to be simultaneously considered and regularly reviewed:
- Technical Controls
- Policy and Documentation
- Process Maturity and Management
A seasoned vCISO is the perfect fit to help develop and sustain a professional and mature security program and is readily available and prepared to undergo the rigor of an audit with confidence. As with any successful project, the first steps of attaining and sustaining CMMC compliance starts with the development of a strategy to build the security program, then formalizing it with relevant security documentation and processes, followed by implementation and enforcement, and lastly, managing the processes to make the process repeatable to ensure the program and practices are institutionalized. Partnering with a vCISO during this process not only helps reduce the risk of failing an audit but also losing out on DoD contract opportunities and revenue.
Knowledge Transfer and Mentoring
From a leadership standpoint, the vCISO can also serve as a mentor to an organization’s existing security team while functioning as the security thought leader, overseeing the execution of their organization’s security affairs. As the program matures, these processes can be reviewed by Jr. IT staff to gain insight into the various disciplines involved with the vCISO role and in some case a vCISO may go as far as to train Jr. IT staff on the proper implementation strategies that have been developed. As the vCISO handles the ‘heavy lifting’, company staff can identify their strengths and weaknesses as they assist the vCISO in whatever capacity is required.
What other benefits can we realize by opting for vCISO?
In short, the role of the vCISO is not constrained to one specific area of focus and can perform tasks that others in the organization do not have the breadth, depth of knowledge or experience to perform. Chief among them include:
- The strategic alignment and approval of the security system frameworks.
- Ensuring that contingency, disaster recovery and business continuity plans are tested and put in place.
- The review and approval of security policies and controls.
- The implementation, testing and approval of the incident response policy and plans.
- Providing or acquiring security awareness training and education content for employees and their security staff – where applicable.
- Advising leadership on matters of risk management, compliance and incident response.
- Assisting with the development of strategies, standard practices, and procedures for cybersecurity and compliance.
- Performing assessments of security functions to ensure compliance with laws, regulations and policies.
- Providing expertise on regulatory and statutory requirements as they relate to security.
- Providing timely and detailed reports of information security and risk-management processes to C-Level officials.
- Being available- in person and live– in preparation to, during and at the conclusion of your audit; from start to finish.
In Summary
Opting to hire a vCISO is the right choice for companies faced with compliance issues for the first time or have been avoiding larger security issues, but intellectually recognize what they must do. For smaller organizations in particular, hiring a vCISO presents an incredible opportunity to unlock all of the benefits of hiring a CISO at a fraction of the cost but with all the benefits. With SMBs budgeting an average of 6.9% on IT and anticipated to increase an additional 38% on cybersecurity, a reputable vCISO doesn’t just guarantee you’re getting the best return on your technology investments, but could lead to a transformational shift that will better align your IT strategy to your compliance requirements. The one thing to keep in mind is that IT cybersecurity compliance requirements will only become more complicated and are going to apply to your organization at some point whether you want it to or not. What you can control is whether or not you’re ready for these changes and a vCISO is how you do precisely that.
Categories
- Backup & Disaster Recovery
- Business Operations
- Case Studies
- Cloud Services
- Cyber Security
- Employee Spotlight
- Finance & Budgeting
- Glossary Term
- Governance & IT Compliance
- Managed Services
- Mobile Device Management
- Network Infrastructure
- NIST 800-171 & CMMC 2.0
- PCI
- Podcast
- Project Management
- TSI
- Uncategorized
- vCIO
Cyber Security Policy Starter Kit:
10 Critical Policies That Every Company Should Have in Place


