Blog

The 5 Most Important Questions to Ask your SIEM Provider & When You Should Probably Re-Evaluate Your Current Solution
First Things First: What is a SIEM?
A SIEM (Security Information and Event Management) is a software solution that collects and analyzes security data from multiple sources in real-time to detect and respond to security threats. It aggregates and correlates logs and alerts generated from different sources, such as network devices, servers, and applications, and uses machine learning algorithms to identify patterns of suspicious behavior or anomalies.
SIEMs also provide a centralized view of an organization’s security posture, allowing security teams to quickly identify and respond to security incidents, such as malware infections, data breaches, and insider threats. The more advanced systems can also automate the incident response process by triggering alerts or taking predefined actions, such as blocking access to a compromised system or quarantining a malicious file.
SIEMs are not only an essential tool for managing security for an organization’s environment, they also help organizations comply with many security and regulatory standards, such as PCI DSS, HIPAA and NIST 800-171. By providing real-time visibility into security events and supporting forensic investigations, they can cover many required security controls required by these standards, all in a single place for a security team.
Why Is a SIEM Critical for NIST 800-171 Compliance & CMMC?
A SIEM system is important for compliance with the NIST 800-171 and CMMC because it provides critical capabilities for monitoring, detecting, and responding to security incidents as required by the DFARS clauses. The capabilities of a good SIEM solution also provide support for a wide range of controls required under NIST 800-171, which can save time for security teams and money for organizations by reducing redundant systems.
Specifically, TSI has found that a properly implemented SIEM can have a large positive impact on an organization’s SPRS score, which we will dig into more shortly. Further, when combined with a managed Security Operations Center (SOC) for 24/7 alerting and coverage, we have seen a massive impact to SPRS and overall compliance, by implementing the right solution and developing the right processes to go along with it.
Why is a SIEM AND SOC Critical for NIST 800-171 Compliance & CMMC?
We come across many instances where an organization seeking compliance mistakenly believes that implementing a SIEM solution is all that is required to address the NIST 800-171 control requirements. Unfortunately, a SIEM solution is only a partial solution without a Security Operations Center (SOC). The SOC is responsible for detecting, investigating, and responding to security incidents. It is the central hub where security analysts monitor network and system activity, identify threats, and coordinate response efforts. In other words, someone needs to be monitoring and responding to each and every alert generated, or a SIEM is simply not helping your organization!
It’s of the utmost importance that regardless of the SIEM solution you select, that you have a 24x7x365 SOC working with your MSP/MSSP to help manage alerts, review and parse through thousands of logs, remediate vulnerabilities and then document the resolution process on your behalf.
Without a SOC 24x7x365, it is impossible for one person or a small team of 2-3 IT employees to properly manage a SIEM as well as review the thousands of daily alerts generated by a SIEM solution. It’s also important to note that as part of the DFARS 7012 requirements, cybersecurity breaches need to be reported within 72 hours of the incident. Without a true SOC in place, identifying, responding to, and remediating the breach and completing all the required reporting and documentation tasks, will be especially challenging- if not impossible- for the organization.
By implementing a managed SIEM and SOC, with a trusted and compliance minded partner organization, businesses can take advantage of the skillset and availability of a Security Operations Center, without having to staff one themselves. Because of this, TSI has found that implementing a managed SIEM/SOC is often the single most cost effective solution when embarking on a NIST/CMMC compliance journey.
What NIST 800-171 Controls Does a SIEM Help Address or Fulfill?
As mentioned earlier, a SIEM system can help address a considerable number of the 110 requirements outlined in NIST 800-171. We have found that on average, a properly implanted solution has helped increase our clients’ SPRS scores by over 50 points. This has a huge impact score wise, and could mean the difference between landing a contract or being passed over.
To help clarify the value of a SIEM solution, here’s a snapshot of the NIST/CMMC controls and control domains most impacted, along with the critical requirements supported.
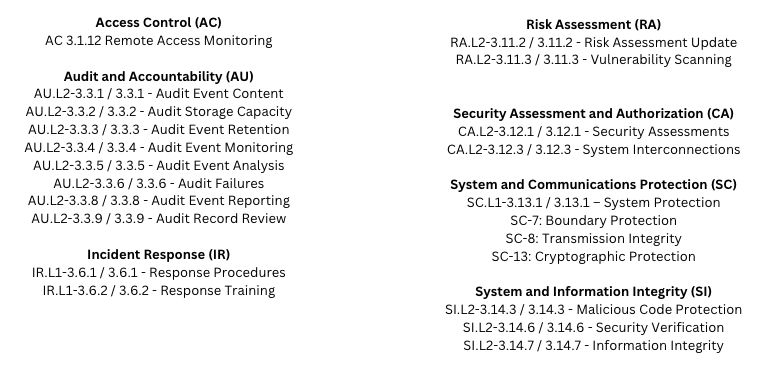
- Continuous monitoring: A SOC with a SIEM can collect and analyze security data from multiple sources in real-time, enabling security analysts to quickly detect and respond to security incidents as they happen, and before they spread.
- Incident response: A well-equipped SOC can quickly investigate security incidents, contain the damage, and recover affected systems and data.
- Access control: By monitoring user activity and identifying anomalous behavior, a SOC can help ensure that any unauthorized access to CUI is reported and then addressed to minimize the potential impact of the breach.
- Audit Retention: A good SIEM solution will include log offload and retention. While required by NIST for compliance, this capability also preserves critical evidence in the event of a breach and keeps attackers from erasing their tracks.
However, it is important to note that a managed SIEM system alone cannot address all 110 requirements outlined in NIST 800-171 and that organizations must implement a comprehensive security program that includes multiple security solutions and practices to achieve full compliance with the standard.
The 5 Questions You Need to Ask Your SIEM Provider Today!
Understanding that we’ve covered quite a bit here, the best recommendation we can make is to start a discussion with your MSP/MSSP and SIEM provider to ensure that they’re able to address your needs ans answer questions in detail. Overlooking such a critically important component of your compliance strategy can significantly impact your ability to adequately address the NIST 800-171 requirements and in the worst case scenarios, result in the loss of contracts or even prosecution under the False Claims Act (FCA). Here are some critical questions to ask a prospective SIEM/SOC provider:
- Does their SIEM solution also have SOC Capabilities? What level of support do they provide?
Ask about the level of support your SIEM provider offers, including their response times for support requests, their availability for critical incidents, and their expertise in specific areas, such as compliance or threat intelligence. This is critically important as DFARS 7012 requires contractors to report cybersecurity incidents within 72 hours. Without a 24x7x365 SOC, you run the risk of meeting these reporting requirements which could result in fines, the loss of contracts and in some serious cases, prosecution under the FCA.
2. What data sources does your SIEM support?
The success of a SIEM implementation largely depends on the variety and quality of the data sources it can integrate with. Ask your provider what types of log files, event streams, and other sources their SIEM can ingest, and make sure they can handle the specific technologies and applications you use in your environment.
3. How does your SIEM detect and respond to security incidents?
A SIEM is only as good as its ability to detect and respond to security incidents. Ask your provider about their SIEM’s detection and response capabilities, including any advanced analytics or machine learning techniques it uses. You should also ask about their incident response process, including how they prioritize and escalate alerts and how they work with your team to investigate and remediate incidents.
4. How do you ensure the integrity and confidentiality of my data?
Your SIEM provider will have access to sensitive log data and information about your organization’s security posture, so it’s essential to ask about their security and compliance practices. Ask about their data protection policies, access controls, and security certifications, such as SOC 2. Please keep in mind that SIEM providers typically cannot see the data, only the logs which typically do not have any data in them. But it is still critical to ask about their data retention policies and how they manage data in compliance with relevant regulations, such as ITAR, GDPR or HIPAA.
5. Can your SIEM scale to meet my organization’s needs?
Make sure your SIEM provider can handle the scale and complexity of your environment. Ask about their performance and scalability capabilities, including how they handle large volumes of data, whether their SIEM can scale horizontally or vertically, and how they handle peak loads.
Conclusion & Informational Resources
It’s evidently clear that a SIEM + SOC solution is a critical component for organizations seeking compliance to NIST 800-171 and CMMC. Overlooking the importance of a fully managed SIEM + SOC solution can significantly impact your organization’s ability to efficiently and adequately address the NIST 800-171 requirements- notably the DFARS 7012’s 72-hour reporting requirements. By asking the right questions and working with a trusted MSP/MSSP and SIEM provider, organizations can significantly improve their security postures and fulfill their contractual obligations with confidence.
To ensure that your SIEM solution meets your organization’s needs and can address the NIST 800-171 requirements, contact us today- we’re here to help!
About TSI
TSI is 34-year old cybersecurity (MSSP) and IT support (MSP) company specializing in helping DIB organizations address their NIST 800-171 and CMMC compliance obligations. As a CMMC-AB Registered Provider Organization (RPO), TSI offers complete NIST 800-171 and CMMC support services to ensure their clients’ sustainable adherence to these expansive compliance requirements. Our team has decades of experience navigating the pitfalls of NIST compliance and would love to help you on your journey. For more information about TSI, please visit our site.
Get in Touch with TSI
For more information on how TSI can help your organization stay compliant with minimal disruption or if there’s anything we can help address, please give us a call at 508-543-6979 or send us a message here to get started.
Categories
- Backup & Disaster Recovery
- Business Operations
- Case Studies
- Cloud Services
- Cyber Security
- Employee Spotlight
- Finance & Budgeting
- Glossary Term
- Governance & IT Compliance
- Managed Services
- Mobile Device Management
- Network Infrastructure
- NIST 800-171 & CMMC 2.0
- PCI
- Podcast
- Project Management
- TSI
- Uncategorized
- vCIO
Cyber Security Policy Starter Kit:
10 Critical Policies That Every Company Should Have in Place


