Blog

DDOS Mitigation Strategies: Lessons From a Recent DDOS Attack
Last month, huge parts of our internet essentially shut down; from Amazon, Twitter, and Spotify, to Netflix and Reddit. One of the biggest takeaways from the attack is the realization of just how susceptible our fragile internet truly is. The graph below shows just how quickly and to what extent the United States’ internet was wiped out.
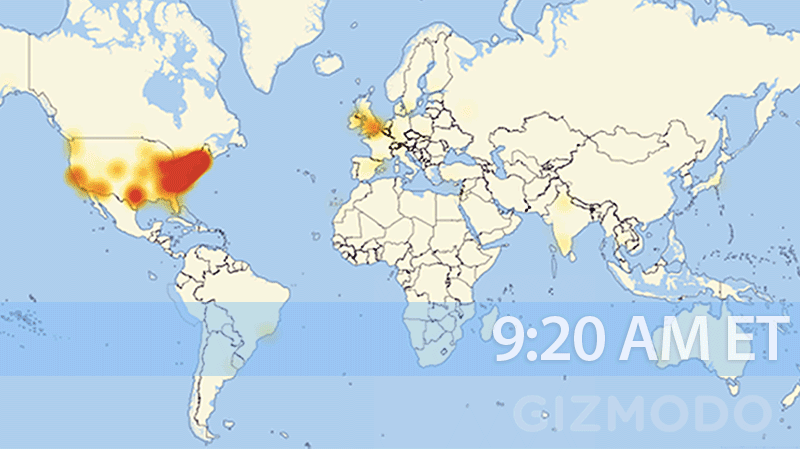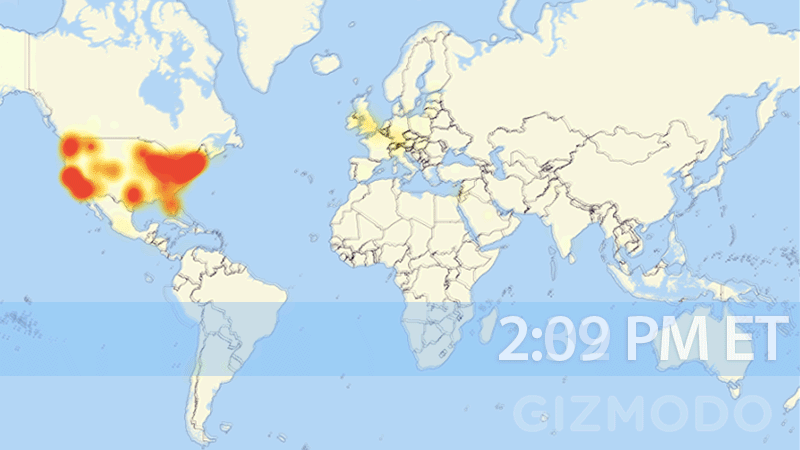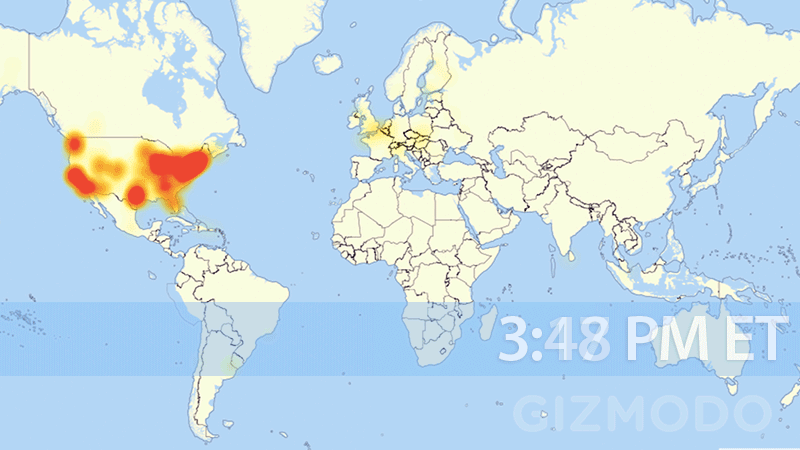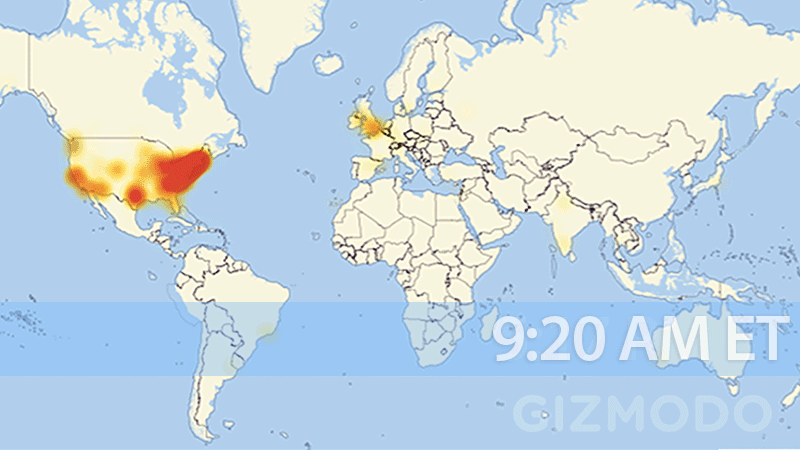
Understanding how the attack occurred, the root cause, and the best ways to help protect from future attacks are all critical questions that need answers.
What Caused the Outage: The cause of the outage was due to a distributed denial of service (DDoS) attack on Dyn, a major Doman Name Servers (DNS) provider. Breaking the process down goes something like this:
- Domain Name Servers (DNS) act as a switchboard operator, directing a request for a site to a specific webpage, ensuring that you reach the correct website you enter in the browser.
- DNS Providers (like Dyn) handles these requests and responsible for managing traffic. Dyn is a major host so any attack directed toward their servers can bring down all the customers they care for.
- DDoS occurrences at the most rudimentary level attack by sending large quantities of junk data to a recipient, which in this case, were Dyn DNS servers. The server becomes overwhelmed by the amount of information being received and begins to slow down significantly, or in some cases, totally shut down.
For an organization like Dyn, the attack was almost certainly more complex in order to successfully bypass internal advanced DDoS mitigation systems.
Enter Mirai Bot: It should be noted that an attack of this magnitude didn’t exactly come out of the blue. Back in September, a full DDoS attack targeted the website of security blogger Brian Krebs after he discussed the feasibility of a full-scale DDoS attacks. The attack utilized source code released by a hacker earlier in the month codenamed Mirai, a malware strain capable of transmitting data at nearly 620 GBPS. Kreb’s site went completely offline until Google stepped in offering protection under their Project Shield initiative.
The Internet of Things (IOT): Kreb later released an article outlining where the power behind Mirai comes from; the Internet of Things (IoT). IoT’s are the “smart” or “connected” devices surrounding our daily lives; from a heart monitor implant to the smart lock that allows you to unlock/lock your front door. Any device capable of autonomously transmitting data to control remotely is considered a part of the IoT domain.
Specifically, Mirai was built to use tens of thousands – if not millions – of hackable IoT devices, left with their protected default passwords. By controlling these devices, Mirai was capable sending so many site requests, it overwhelmed servers of a provider as large as Dyn.
Tips from the Experts: Following the unprecedented attack, the Department of Homeland Security issued a warning to users and administrators on steps to follow to ensure your IoT devices are not hacked:
- Ensure all default passwords are changed to strong passwords. Default usernames and passwords for most devices can easily be found on the internet, making devices with default passwords extremely vulnerable.
- Update IoT devices with the latest security patches as soon as they are made available.
- Disable Universal Plug & Play (UPnP) on routers unless necessary.
- Purchase IoT devices from companies with a reputation for providing secure devices.
- Be aware of the capabilities of the devices and appliances installed in your home or business. If a device comes with a default password or an open Wi-Fi connection, change the password and only allow it to operate on a home network with a secured Wi-Fi router.
- Understand the capabilities of any medical devices intended for at-home use. If the devices transmit data or can be operated remotely, it has the potential to be infected.
- Monitor Internet Protocol (IP) port 2323/TCP and port 23/TCP for attempts to gain unauthorized control over IoT devices using the network terminal (Telnet) protocol.
- Look for suspicious traffic on port 48101. Infected devices often attempt to spread malware by using 48101 to send results to the threat actor.
Learn More: To learn more on how to properly protect your network and identify vulnerable devices used in DDoS attacks, Contact Us today!
Confident with Your IT Strategy?
If you found the information in this blog post helpful and you'd like to discuss your business' technology strategy, then we'd be happy to hear from you.
Categories
- Backup & Disaster Recovery
- Business Operations
- Case Studies
- Cloud Services
- Cyber Security
- Employee Spotlight
- Finance & Budgeting
- Glossary Term
- Governance & IT Compliance
- Managed Services
- Mobile Device Management
- Network Infrastructure
- NIST 800-171 & CMMC 2.0
- PCI
- Podcast
- Project Management
- TSI
- Uncategorized
- vCIO
Cyber Security Policy Starter Kit:
10 Critical Policies That Every Company Should Have in Place


