Blog

10 Questions to Validate Your Backup and Disaster Recovery Strategy for Business Continuity
A backup and disaster recovery strategy is exactly what it sounds like: a plan for how you’re going to restore all of your critical electronic information in the event that you suffer from some type of disaster. If your office burns to the ground, this strategy will allow you to pick right up again at a secondary location as if nothing ever happened – at least as far as your productivity and data integrity are concerned.
But the difference between a backup and disaster recovery strategy and the right strategy to address the unique needs of your business is a large one, indeed. If you truly want to validate your backup and recovery strategy and guarantee that your business is as protected as you think it is, there are a few key things you’ll need to keep in mind.
Are Your Backups Encrypted At Rest as Well as In Transit?
Encryption is a method used to protect your data from prying eyes by converting raw information into code. Without an encryption key, even if someone were to download a file from your server, they still wouldn’t be able to access the important information contained inside.
However, your data needs to be encrypted at all times for an adequate backup and disaster recovery strategy – that means both while it is being uploaded to or downloaded from your server, as long as while it is sitting idle without anyone accessing it. In transit encryption is great, but it won’t stop someone from stealing what’s important to you if they gain access by hacking into a device in your environment.
Have You Established Both an RTO and RPO For Your Company?
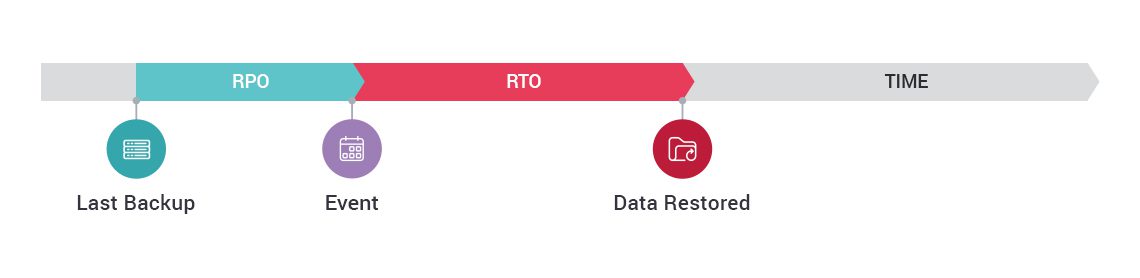
RTO is short for “Recovery Time Objective” and refers to the total amount of time that can go by before your critical business processes MUST be restored, or you’ll begin to experience unacceptable losses to your core functions.
RPO is short for “Recovery Point Objective.” Based on your unique business, it’s the amount of data you can tolerate to lose and still restore your server to a point before that breach or disaster occurred. It’s particularly important in terms of ransomware attacks.
Do You Have Data-Based or Image-Based Backups?
An image-based backup saves all of your critical data in a single file, called an image. This essentially backs up everything – including both deleted files and empty disk blocks. When you restore from an image, you’re essentially restoring from a carbon copy of your original storage drive.
Data-based backups, on the other hand, allow you to restore individual files and folders during the recovery process. This is ideal for situations where you may not have lost everything and thus don’t need to restore all of a particular drive or server. Both let you achieve the same goal in two totally different ways, so it’s critically important to know which of these you actually employ.
Image-based backups are far more modern and recover environments far faster than data-based backups. In most instances, data backups will require a complete rebuild that will entail acquiring new licensure and, because of that, can take as long as a week to get back to any semblance of normal operations.
How Long Will It Take You to Actually Recover From a Disaster?
It’s one thing to look at your backup and disaster recovery strategy on paper and say “based on these steps, it should take us X amount of time to fully restore everything and get back up and running.” However, it’s always best to not assume that the specs will live up to their expectations.
You need to know, beyond the shadow of a doubt, how long it will take you to get back on your feet after a disruption and the only way to do that is test your plan before a disaster to help guarantee that it actually works the way you think it will. Partnering with an organization like TSI can help you conduct a series of drills that will test your strategy against various scenarios to guarantee that your expectations and the capabilities of your backups are properly aligned.
Along the same lines, routine quarterly testing is also important – although it’s also different from a complete backup and disaster recovery test. Instead of testing your entire strategy, this will require you to test every restore option you may use, making sure that all backup and restore techniques work as you expect them to.
Does Your Backup’s Performance Comply With any Compliance Needs, or Client-Driven Compliance and/or Service Requirements?</strong
HIPAA, for example, has a number of specific rules about how patient health information can be stored, shared and accessed. Data backups, by their very nature, fall under these guidelines. For your backup and disaster recovery strategy to be effective, you need to make sure that it’s compliant with any rules or regulations governing your industry.
If you’re providing services for a client, it must also be compliant with rules and regulations in THEIR industry as well. Thanks largely due to a general (and much needed) change in attitudes about security and an emphasis on safeguarding data more proactively and vigilantly, oftentimes your own clients are very concerned about these types of compliance requirements – which means that you need to be concerned about them, too.
Where Is Your Data Being Hosted?
Even though your data is “in the cloud,” it’s still physically stored somewhere. Even if your provider is in the United States, their servers might be in China. Where your data is being hosted dictates who has access to your data in a physical sense and different countries take physical data security with varying degrees of seriousness.
This also ties directly into the previous question about compliance. Some compliance requirements are very clear that they do NOT want any customer data (or your data) hosted outside of the United States or North America. If you don’t know where your data is hosted, you cannot be sure that you’re in compliance.
Have You Confirmed That the Data You’re Backing Up is Free of Vulnerabilities and Corruption?
If a file became corrupted when it was stored locally, even the best backup and disaster recovery strategy in the world isn’t going to help you get that data back after a disruption. You need to have policies and procedures in place to guarantee data integrity, helping to make sure that this is something you don’t have to worry about.
At least on a quarterly basis, you should do a test of your currently saved data by restoring a small number of files and folders. Then, you can manually check that data to verify that it could actually be used in the event of a disaster and that your backups are working as you need them to. Likewise, do a hardware check to make sure that no assets (particularly hard disk drives) have failed since you last used them.
Data duplication and redundancy are also techniques that will help make sure you’re not being held back by these vulnerabilities, and can mitigate their chances of impacting your environment.
Are You Aware of the Difference Between Replication, Duplication and Redundancy?
Yes, it’s true – these are three different terms and should always be treated as such.
Data replication is the process of storing information in more than one place, helping to improve its overall availability. In the event that one source of your data is inaccessible or otherwise destroyed, you still have copies stored at another location that you can draw from.
Data duplication lets you easily create backup copies of files, folders and other important information for the purposes of recovery. This guarantees that if your primary copy of a particular file is lost, you still have an up-to-date copy that you can use to recover that information, that work and those ideas.
Data redundancy involves the existence of data that is considered to be additional beyond your actual data. This can be a complete copy, or select pieces of information that allow you to detect errors in those original files or reconstruct damage files up to a certain point in their history. In terms of a viable backup solution, this essentially acts as an extra layer of protection to reinforce not just the data being backed up, but the effectiveness of your backup strategy as a whole.
Is Your Backup and Disaster Recovery Strategy Documented?
If you task one person with coming up with your backup and disaster recovery strategy and that person leaves your company, you shouldn’t have to start all over. Every step of your strategy should not only be documented, but in a way that is easily repeatable for anyone who happens to be present during a disaster.
Are You Testing Your Strategy on a Regular Basis?
Your business’ technology is going to continue to grow and evolve over time. Because of that, your backup and disaster recovery strategy needs to do the same. It is not written in stone and is instead a fluid document, something to be changed and improved several times a year.
As certain gaps in coverage or vulnerabilities are created over time, you need to make sure that you’re testing your strategy on a regular basis. This will help identify areas where your current plans come up short in terms of protection, allowing you to fill those gaps and address those problems before the time comes where you’re faced with a genuine disaster and a viable plan becomes critically important to your business’ survival.
Likewise, as certain businesses continue to grow, their priorities regarding what data is important will change – which means that their backup needs can and should change right along with them.
Confident with Your Backup Strategy?
If you found the information in this blog post helpful and you'd like to discuss your business' backup and disaster recovery strategy with a security expert, then we'd be happy to hear from you. Find out how TSI can help your business.

Categories
- Backup & Disaster Recovery
- Business Operations
- Case Studies
- Cloud Services
- Cyber Security
- Employee Spotlight
- Finance & Budgeting
- Glossary Term
- Governance & IT Compliance
- Managed Services
- Mobile Device Management
- Network Infrastructure
- NIST 800-171 & CMMC 2.0
- PCI
- Podcast
- Project Management
- TSI
- Uncategorized
- vCIO
Cyber Security Policy Starter Kit:
10 Critical Policies That Every Company Should Have in Place


